In 2016, the group started timidly and learned the cords through other hackers. It has since stealed at least 4.2 million dollars, first from banks in the former Soviet Union, followed by victims in Europe, Latin America, Africa and Asia. Group-IB researchers, a Singapore-based attack prevention cybersecurity company, tracked the Silence early and judged Silence’s members to be familiar with the safety activities of White-Hat. A study last year outlines the roles, abilities, failures and effective bank heists of Silence hackers. Researchers were aware of bank jobs in September 2018 that brought the company more than $800,000. In today’s fresh study, the Group-IB shares more information about the tactics, methods, and processes of hackers to assist other investigators identify and properly attribute assaults early.
New instruments and tactics
Silence has enhanced its operational safety and altered its tool kit to prevent detection. Besides rewriting the first-stage module (Silence. Downloader / Truebot), the group started using a PowerShell-based Ivoke fileless loader. A fresh PowerShell agent, called EmpireDNSAgent (EDA) is used to laterally move the victim network since it is based on the newly deserted empire system and the dnscat2 project. In October 2018, Silence began sending recognition emails to prepare for an attack. Such a message would be useless and would appear to be an automated response to an unsuccessful shipment.
The purpose was to receive from the target an updated list of active email addresses. Silence sent more than 170,000 e-mails to Asia, Europe and post-Soviet nations during three distinct campaigns against victims, claims Group-IB.
Victims on nearly every continent
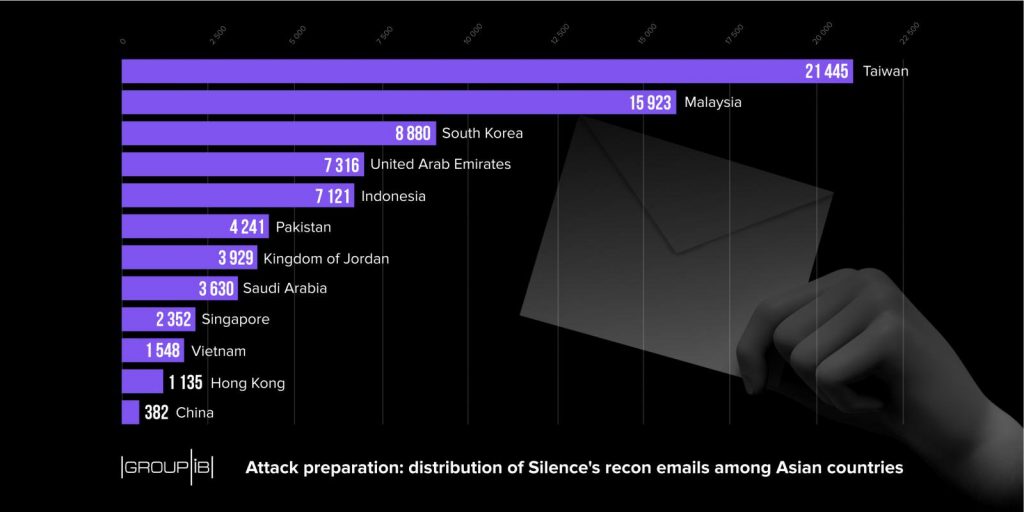
When expanding to Asia, the hackers shipped around 80,000 emails to destinations in 12 nations that had failed to deliver. As seen in the picture below, Taiwan, Malaysia and South Korea are the major targets. The campaign for the recondition of European financial institutions was the lowest, with less than 10,000 messages. The focus was on UK financial firms.
After validating email addresses, the actor moves to the next steps of the attack to send a payload message downloading Silence-specific malware. Self-developed tools or binaries are now available on the target system for persistence and lateral movement. The attacker reaches the card processing device at the end and can control ATMs with a trojan atmosphere or a program called xfs-disp.exe to distribute cash to money mules at certain times.
Silence hard at work
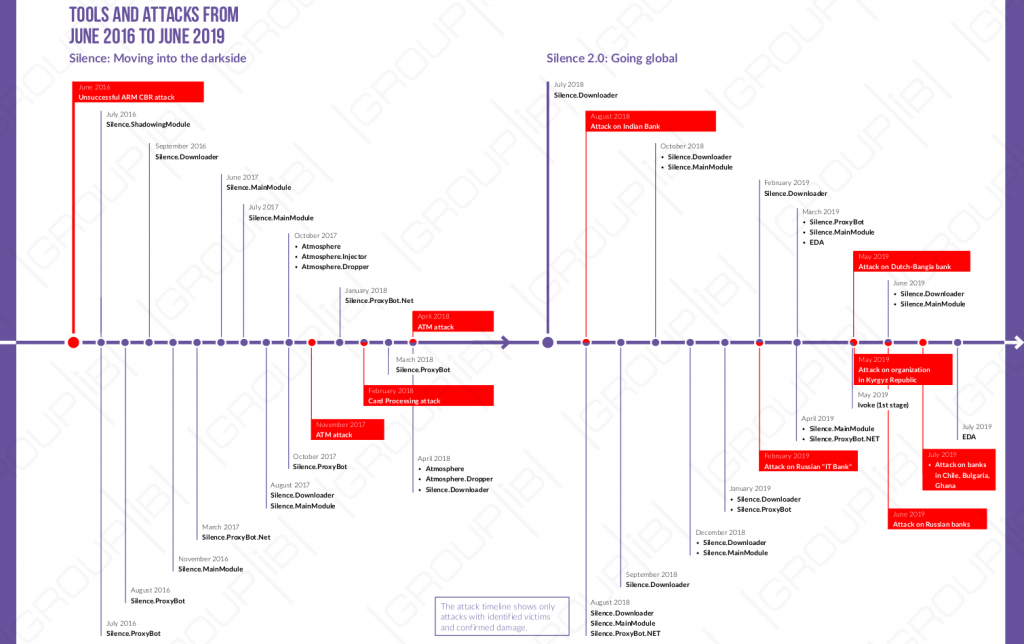
The last Silence Activity Report of the Group-IB includes the period from 28 May 2018 to 1 August 2019. Investigators trace attacks, recognition and phishing campaigns against banks mainly in Russia. The hackers used all the resources and possibilities. As such, they took advantage of the absence of the Sender Policy Framework (SPF) to impersonate a real bank and sent messages from the central bank of the Russian Federation in another cap. In early 2019, the Silence group began moving towards European objectives and assaulted a financial organization in the UK. They have sent a file with a valid SEVA Medical LTD signature. However, they have not shifted focus from Russian banks. By February the threat actor had compromised Omsk IT Bank and, according to public reports at that time, was able to steal approximately 400,000 dollars. At the end of May, Bangladesh news outlets reported that several masked men withdrew $3 million or more from cameras belonging to the Dutch Bangla Bank. These were cash mules and the CCTV system registered them. Security camera footage demonstrates how you insert the card into the ATM and wait until the cash comes out.
Researchers think that the ATMs were controlled by the Atmosphere Trojan or’ xfs-disp.exe’ because no malware was discovered in cash machines. Silence characteristics of Group-IB assaults have been effective in Chile, Bulgaria, Costa Rica, Ghana and India. Silence depends on strong instruments that are not used by other organizations and continues to adapt its game to take safety alternatives and scientists forward.
Group-IB believes there might be a link between Silence and TA505, a second group using FlawedAmmyy. Downloader to target financial-sector victims. “A comparative analysis of Silence.Downloader and FlawedAmmyy.Downloader revealed that these programs were developed by the same person – a Russian speaker who is active on underground forums.” But this is where the common ground ends, as TA505 utilizes a totally distinct operational infrastructure. Rustam Mirkasymov, Head of Group-IB Department for Dynamic Malware Analysis, tells the inexperienced group which the firm began monitoring three years ago no longer exists. The group “evolved into one of the most sophisticated threat actors targeting the financial sector not only in Russia, but also in the Americas, Europe, Africa, and especially Asia,” says the researcher.