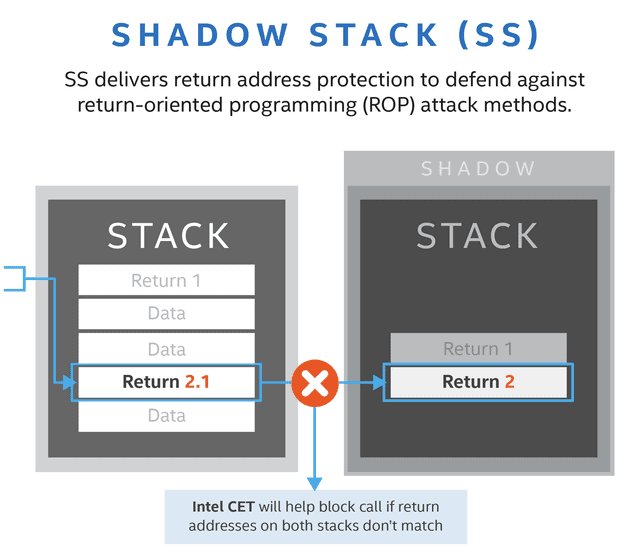
Initially, the latest Control-Flow Enforcement Technology (CET), which is integrated into the hardware microarchitecture, will be available in the upcoming Tiger Lake mobile processors, but the tech giant aims to use it in future as well in desktop and server platforms. Intel CET has two main components: indirect branch tracking (IBT) which will protect against jump-oriented programming (JOP) attacks and call-oriented programming (COP) attacks; and shadow stack (SS) which provides return address protection from return-oriented programming (ROP) attacks.
In order to achieve its goals, malware often relies on control-flow hijacking and many pieces of software are plagued by memory security issues that enable these types of attack. Intel analyzed data from Trend Micro’s Zero Day Initiative (ZDI) and found that this group contained nearly two-thirds of the 1,100 vulnerabilities reported last year. Intel noticed that CET specifications were released in 2016, and partnered with Microsoft to create better protection against these types of attacks. Windows 10 users will be able to take advantage of CET ‘s security through a feature called Hardware-enforced Stack Security which is currently available in the operating system’s Insider Preview version. “This new Hardware-enforced Stack Protection feature only works with Intel CET instructions on chipsets. It is based on a new CPU architecture which complies with Intel CET specifications. For applications running on an OS supporting Intel CET, users should receive comprehensive guidance from our partners on how to ‘opt-in’ protective applications,” explained Tom Garrison, VP of Intel’s Client Computing Division and GM Security Strategies and Initiatives. Intel also noted that CET expands the Hardware Shield feature ‘s threat security capabilities present in vPro platforms.